Securing the ARM
This ARM enables operators to secure routing management.
HTTPS, for example, protects users against man-in-the-middle (MitM) attacks launched from compromised networks; with MitM attacks, hackers can steal sensitive enterprise information.
SSH, for example, uses encryption to secure transfer of information between client-server; it allows users to execute shell commands on a remote device with the same level of security as if working in the accessed device.
| ➢ | To secure the ARM: |
| 1. | Open the Security page (Settings > Administration > Security). |
Security Page
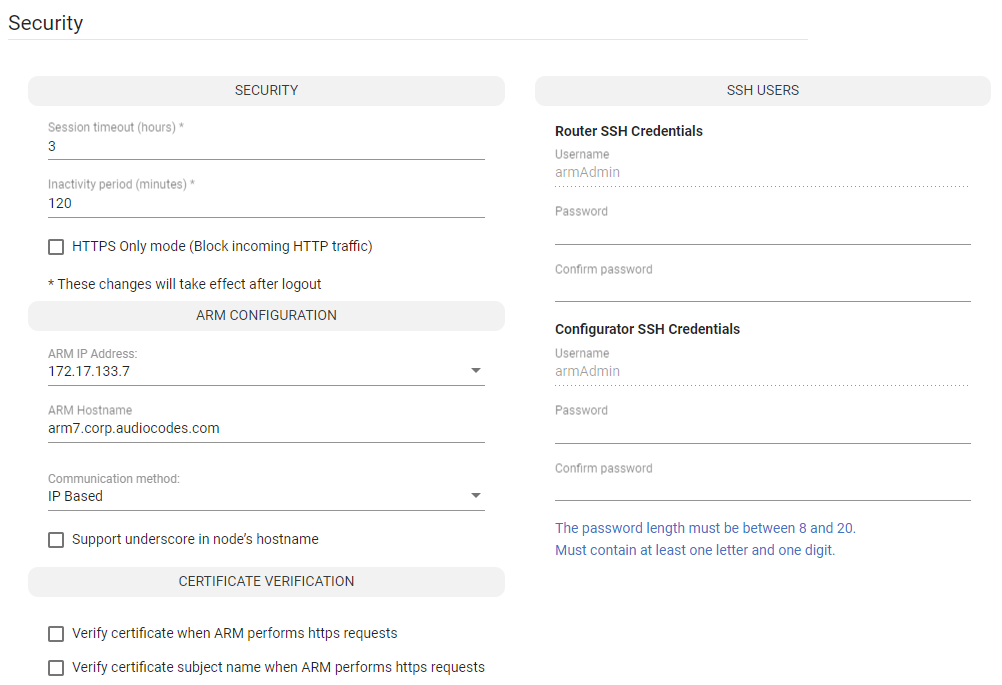
| 2. | Use the following table as reference. |
Security Settings
| Setting | Description |
|---|---|
|
Session timeout (hours) |
After n hours, the user will be logged out, irrespective of whether they're active or inactive. The user will be forced to reenter their password (to reopen the session) if the timeout you define (in hours) expires. |
|
Inactivity period (minutes) |
If the user does not interact with the GUI for n minutes, they will be redirected to the login screen and will need to reinsert their password. 0 disables the feature; inactivity will not impact the user's account. |
|
HTTPS Only Mode |
Disables HTTP. Enables HTTPS only for ARM Configurator / ARM Router. |
| 3. | See Enabling Client Side Certificate Validation and Enabling Certificate Subject Name Verification and click Submit. |